Sharp leaders deploy it, improv performers embrace it and fifth generation (5G) wireless technology depends on it. I’m referring to the power of “and.”
Skim through any thought leadership concerning 5G’s massive potential to generate new business models and related benefits — remote surgery, connected sports stadiums, smart cities, transformed supply chains, autonomous driving and much more — and you’ll see that conjunction attached to 5G: 5G and edge computing, 5G and artificial intelligence (AI), 5G and Internet of Things (IoT).
5G’s blazing speed, low latency and jaw-dropping capacity (its ability to connect to far more devices and sensors — millions more — in a small area, compared to 4G) becomes genuinely game-changing when combined with other advanced technologies.
“Taken alone, these technologies have enormous potential in their own right, but combined, experts say, they have the power to transform industrial technology on a scale not seen since the advent of steam power,” James Rundle and Angus Loten note in the Wall Street Journal. “The key ingredient, the experts say, is 5G. It gives developers the ability to scale up projects more easily because there’s no need to build extensive fiber-optic networks to keep data flowing. What’s more, 5G networks let internet-connected devices transmit much more information much more quickly—which in turn is spurring developers to come up with more advanced machines that can take maximum advantage of the capability.”
That translates to better pandemic-tracking, faster drug-development cycles, far more reliable and efficient factories, and even tastier beverages, Rundle and Loten point out. While 5G and IoT can fuel breakthroughs like the Beer Fingerprinting Project, those combinations of advanced technologies also produce new sets of risks to be managed, inside of companies and throughout the third-party ecosystem.
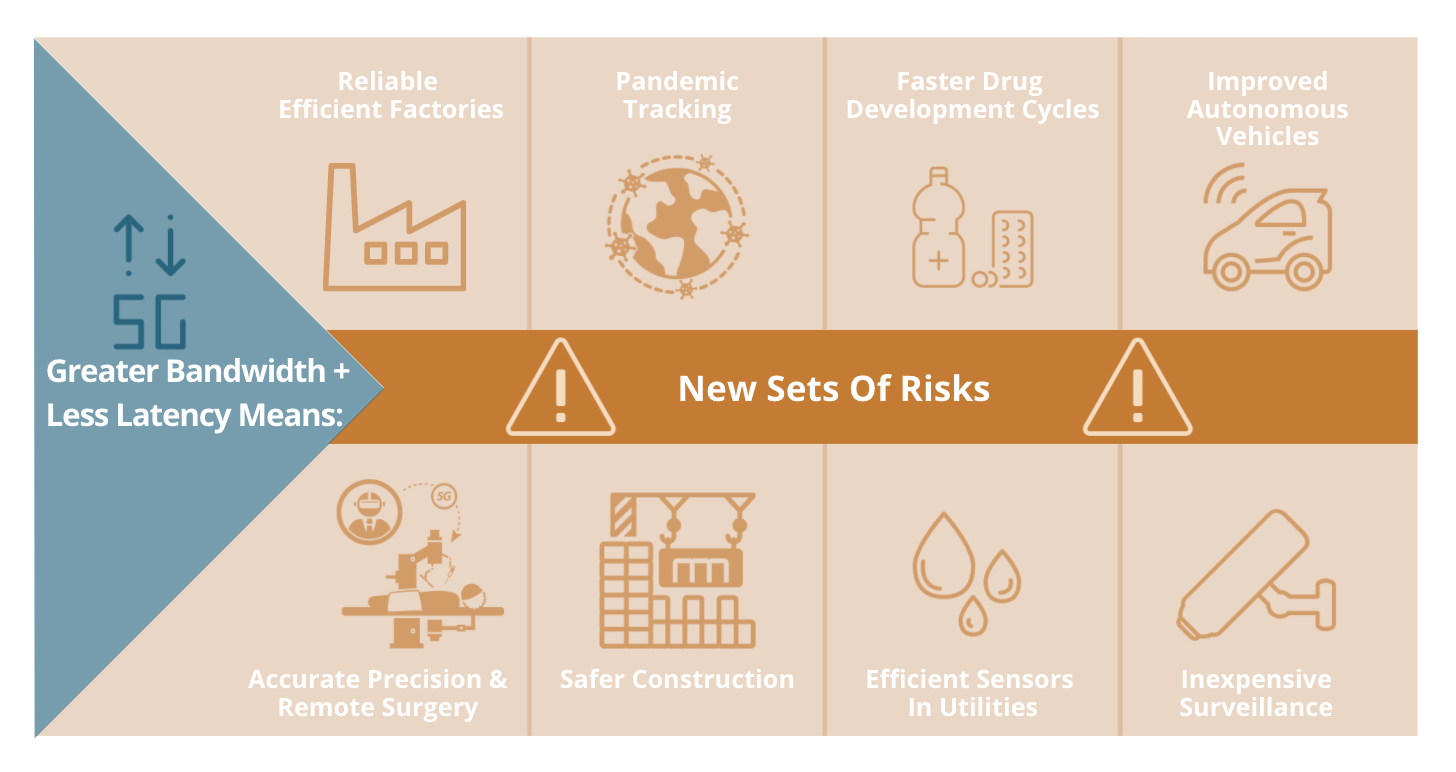
Shared Assessments Senior Advisor Charlie Miller notes that it is important for third party risk management professionals and vendors to protect the 5G ecosystem with tools and mechanisms such as continuous real-time monitoring, IoT approval and certification, and related supply chain standards. Miller also points out that 5G networks, with their large capacity, are ripe for larger, more complex cyberattacks (he also explains why current 5G security needs rethinking).
Of course, 5G security and 5G privacy (which Shared Assessments’ Tom Garrubba discusses here) comprise only one part of the risk management challenge. Risks generated by edge computing, AI, IoT and other technologies that follow “5G and…” utterances also need to be addressed.
The latest IoT risk research in the ongoing collaboration between The Ponemon Institute and Shared Assessments, “A New Roadmap for Third Party IoT Risk Management,” sheds light on this need. Some of the survey report’s extensive findings show that many third party IoT risk management efforts currently suffer from:
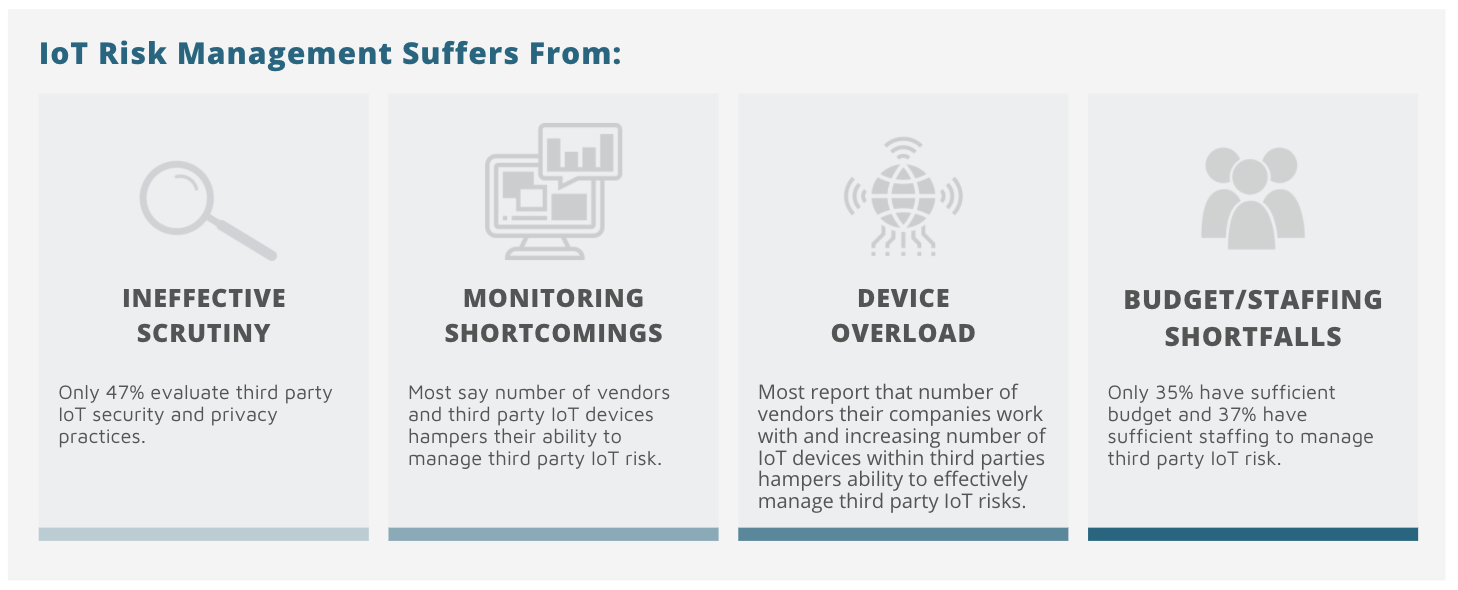
- Ineffective scrutiny: Only 47% of respondents evaluate third party IoT security and privacy practices before working with those parties.
- Monitoring shortcomings: Less than one-third monitor the risk of IoT devices used by their third parties.
- Device overload: Most respondents report that the number of vendors their companies work with as well as the increasing number of IoT devices within third parties hampers their ability to effectively manage third party IoT risks.
- Budget and staffing shortfalls: Less than four in 10 respondents report that sufficient budget (35%) and sufficient staffing (37%) are allocated to managing third party IoT risks.
The report also identifies a broad range of leading practices that can help strengthen IoT security as well as the management of third party IoT risks.
Improv performers often respond to their colleagues dialogue by saying, “Yes, and…” because the reply helps sustain the momentum of the comedic scenario they’re creating together. Leadership experts encourage executives to replace their use of the conjunction “but” with “and” as an invitation to mutually work through a problem (as opposed to posing an obstacle).
Third party risk managers will need to embrace a similarly collaborative approach on problem-solving as the use of 5G networks, related technology and 5G-related risks increase.
